Secure browsing for Enterprise
be.Safe essentials filters out undesired content due to preferences. It allows enterprises and organizations to protect their business from internet threats or non-business -related use of the internet.
Easy & simple cybersecurity for enterprise

be.Safe essentials is possibly the easiest way for enterprises and organizations to control cybersecurity risks and content policies for their employees. It benefits CSPs and users alike.
- Secure browsing: internet browsing protection, web search, content control and anti-adware.
- Malware protection: automatically detects, classifies and blocks malware.
- Comprehensive analytics and productivity feedback.
- Omnichannel and user friendly through mobile app or website.
- CPE agnostic – compatible with 99% of current SMBs.
The cyberthreat facing enterprises

Today, almost all organizations, regardless of size or sector, use the internet in their daily activities. This creates increasing concern about how employees, clients are going online, and the level of multiple threats they are being exposed to.
Enterprises, while seeking protection from external internet threats, are also concerned about internal, non-business-related use of the internet. This both reduces productivity and increases threat exposure. Similarly, educational establishments must protect students while detecting inappropriate Internet usage.
Other scenarios relate to public transport companies, hotels, or restaurants which offer Wi Fi to their customers. Such businesses must avoid inappropriate or illegal activity which could impact their image.
Such organizations can turn to carrier service providers to deliver suitable cybersecurity solutions – but these solutions must be both cost-effective and amenable to management by non-technical users.
What are the important points related to be.Safe essentials

Internet threats against organizations
With ever more numerous and sophisticated cyberattacks, even small organizations must protect their business continuity and legal compliance – but they need a solution that they can afford and understand.

Improving visibility is an essential start
As more organizations adopt direct internet connections and users bypass the VPN on line, DNS-blind spots are created. Monitoring DNS requests and subsequent IP connections improves security visibility and network protection.
Leading threat intelligence dictionary
Updating the information related to threat intelligence from the world’s leading BrightCloud dictionary is essential for discovering and blocking a large number of malicious IPs and domains. Having daily protection in place prevents out-of-date and security issues from occurring.

Security strategies improve productivity
Security strategies can also help with monitoring, understanding, and improving productivity. Unproductive traffic can be monitored and filtered, while reports about usage and protection statistics are generated periodically.
Understanding cybersecurity for enterprises
As cyberattacks proliferate, cybersecurity is becoming increasingly important for companies of every size. All are vulnerable to attack, and all are required by law to keep their customer data safe. Therefore, every company needs some level of cybersecurity solution deployed in their network to guarantee both business continuity and legal compliance.
SMBs, however, are hindered in adopting cybersecurity by budget and knowledge constraints. Around half the respondents to a Deloitte study cited a lack of both budget and staff as a barrier to effective security protection, while a similar proportion also noted increased sophistication in cyber threats.
A cost-effective security strategy, for any type of enterprise or organization, starts with improving visibility. As more organizations adopt direct internet connections and users bypass the VPN, DNS-blind spots are created. Monitoring DNS requests as well as subsequent IP connections is an easy way to provide greater accuracy and detection of compromised systems, improving security visibility and network protection.
Accessing threat intelligence from a leading threat intelligence dictionary is essential for discovering and blocking a broad spectrum of malicious domains and IPs. This malware protection can prevent out of date security breaches, and block malware by categories.
Security strategies can also help with monitoring, understanding, and improving productivity. Daily productivity can be compared with average and maximum values, and productivity profiles can be customized per department. Unproductive traffic can be monitored and filtered, while reports about usage and protection statistics are generated periodically.
A security service can be deployed as a cloud SaaS, managed by the supplier to avoid installation and maintenance costs. Alternatively, it can be a virtual machine deployed on proprietary hardware or in the cloud, or as a VM software package installed on DNS servers connected by service chaining.
Teldat Solution & Product be.Safe essentials
The Teldat be.Safe essentials basic cybersecurity solution
be.Safe essentials is the perfect tool and service for companies with low cybersecurity budgets. It provides the first level of security without need for future investment. It is a must for cybersecurity while being affordable for everyone. It can be consumed aaS, meaning no requirement for deployment, hardware, or cybersecurity knowledge.
No additional hardware and easy to set up

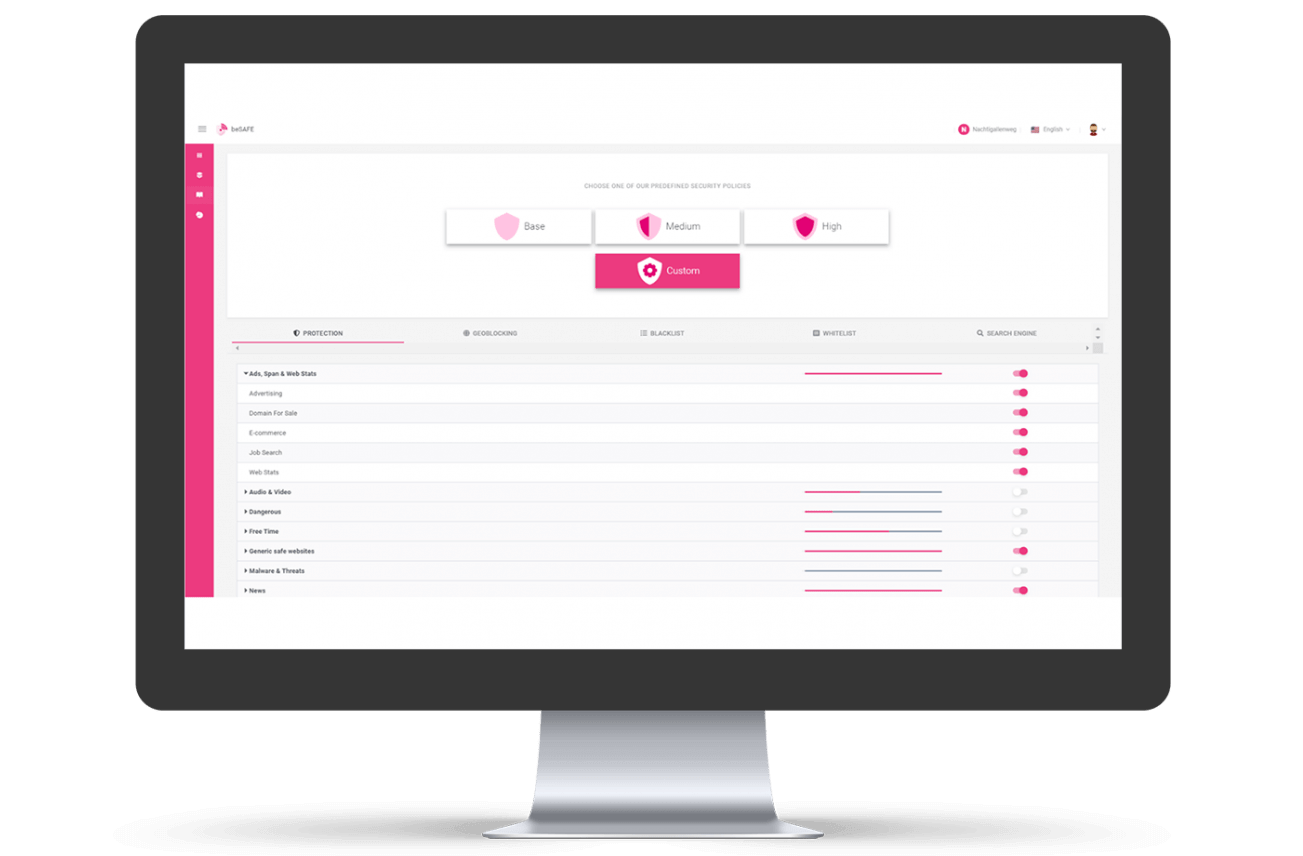
be.Safe essentials is a Web Filter solution based on 84 Categories grouped into 10 Families. Its innovation lies in its optimization for companies and organizations with low security budgets and no knowledge of security. As a basic security solution, be.Safe essentials is very easy to understand and configure. Anyone can set it up, even without security or technical knowledge.
be.Safe essentials needs no additional hardware, because it is based on standard DNS and DyN DNS technology. Compatibility with 99% of all customer CPE devices is guaranteed – firewalls, routers, access points, or even computers. be.Safe essentials can be deployed on any enterprise or organizational installed base. Teldat delivers the solution aaS which is nearly plug & play.
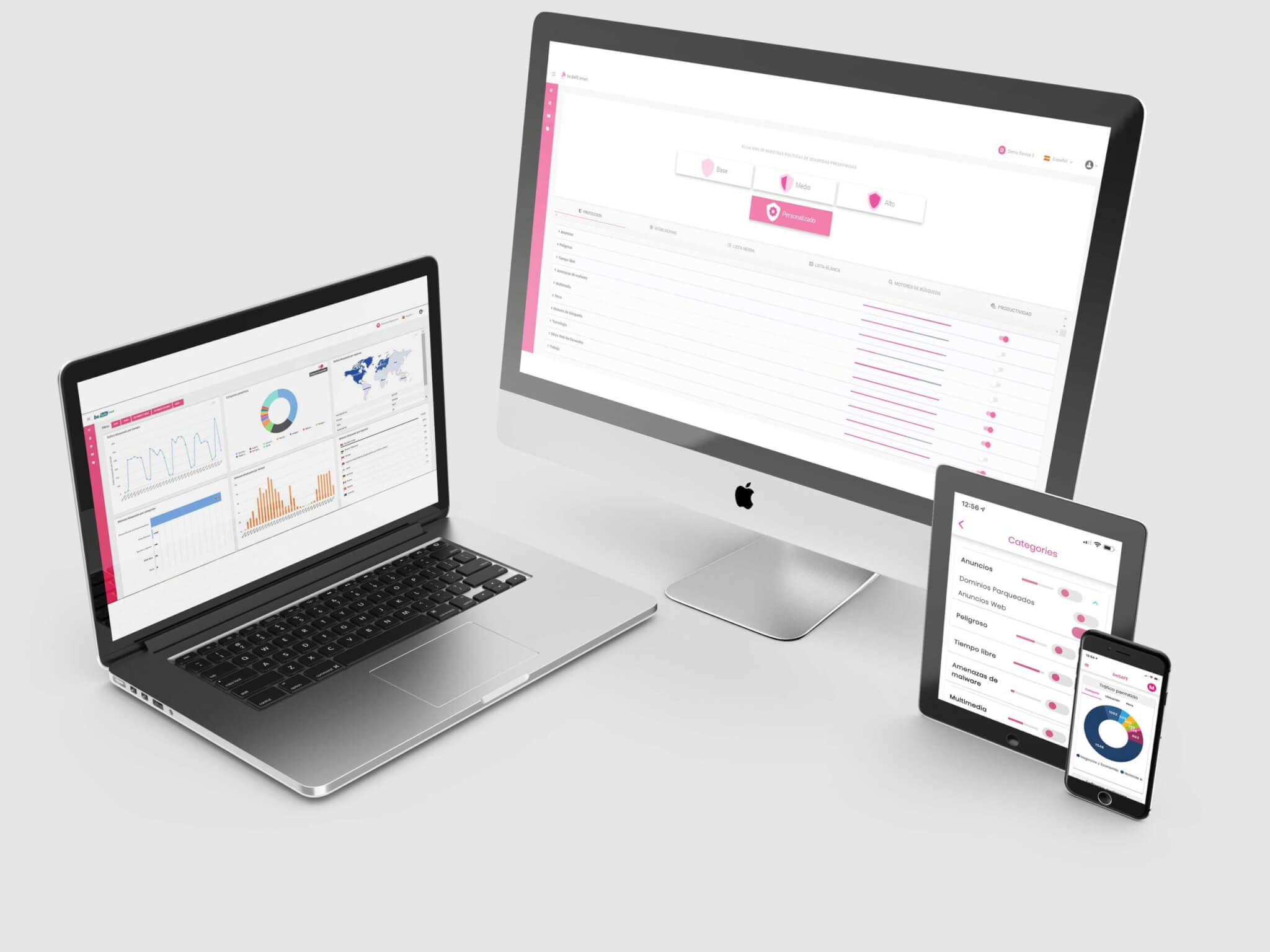
Omnichannel user interface
Once installed, be.Safe essentials is easy for low budget companies to use, as Teldat’s omnichannel user interface is available through both a web page and totally free iOS and Android mobile apps which allow users to manage every aspect of be.Safe essentials from their mobile phones in any location. This easy-to-understand user interface allows users to configure cybersecurity policies in seconds (minutes?) without deep cybersecurity knowledge.
Powerful Threat Intelligence Dictionary

Although be.Safe essentials is a basic cybersecurity solution, it is nevertheless empowered by a world-leading Threat Intelligence Dictionary. It can automatically detect, classify, and block malware threats in the network. Malware detection is categorized by the threat nature, and automatic blocking is based on reputation IP and malicious URLs. With zero-day protection, the dictionary is updated continuously, every minute, to register any malware event in the world, so eliminating out-of-date security breaches.
Visibility and productivity
The interface uses widgets to simplify understanding of what is happening in a network. It can detect usage patterns, how many sites were blocked and when, and what malware types were detected on these sites. Similarly, any region can be blocked at any time. Every user can customize the interface to their specific needs. be.Safe essentials becomes a powerful and intuitive security tool for companies or organizations wishing to block dangerous or inappropriate websites.
be.Safe essentials also has a productivity module which can be configured to favor websites that benefit the business’s productivity, with ‘one click’ checking of current productivity. Additionally, daily productivity results can be compared with average and maximum values to highlight anomalies.

Highly cost-effective for resellers

be.Safe essentials enables any IT reseller or Carrier Services Provider (CSP) to reach all potential customers, providing internet security protection services without additional investment, support centers or training programs.
Use cases
Public administration
Some public administrations give the public access to their services via the internet.
Public transport companies
Transport companies which offer internet connectivity as a service to improve competitiveness and operational efficiency
Challenge
Road and rail public transport companies need onboard connectivity via 4G/5G and Wi-Fi. This allows management and monitoring of their vehicles, as well as providing security and benefits for their passengers.
However, the wireless SD-WAN needs security protection against both external malware infections and security breaches, and internal misuse by passengers – yet deploying a security solution to each vehicle and integrating it with the onboard CPE potentially creates a massive deployment and configuration effort. The effort of adding security, and then keeping it updated after installation, should be kept as simple and as low-cost as possible.
Security solutions should also provide analytics and productivity feedback to allow ongoing improvement as well as immediate protection.
Solution

be.Safe essentials is CPE agnostic, and will be readily compatible with the on-vehicle CPEs. It can be configured through a website or mobile app.
Its web filtering is empowered by a leading Threat Intelligence Dictionary that provides updated categorization of 90% of websites worldwide according to content categories and geographies. It offers default profiles to facilitate configuration policies.
be.Safe essentials can detect usage patterns about how many sites were blocked and when, and types of malware detected. Additionally, any region can be blocked at any time.
It provides content control based on 84 categories grouped into 10 families: Ads, Dangerous, Free Time, Malware & Threats, and Others.
Why Teldat?
With its omnichannel user-friendly interface, be.Safe essentials allows users to configure cybersecurity policies in seconds, without deep cybersecurity knowledge. It provides comprehensive analytics and productivity feedback to inform performance improvement. At the same time, it offers a cost-effective solution.
Public administration
Some public administrations allow access to their services via the Internet. It is convenient, although there are security implications.
Challenge
Users interact with public administrations through web or API services.
However, it is likely that other machines or processes will use internet-facing services. A service’s users are probably not limited to staff or customers. System integrators, third party suppliers, managed service providers, home workers, and process orchestration tools like those used in development pipelines could be considered ‘users’ of a service.
An Authority’s internet-facing services will likely also be impacted by both planned and unplanned events. Even if the service is neither attacked nor fails, it will need to be regularly updated and maintained.
Protection from these scenarios with a low-cost solution which is easy to deploy and manage is essential.
Solution

be.Safe essentials is a user-friendly solution that allows public administrations to control their cybersecurity risks and content policies for their staff, users, and other parties. Content control is based on 84 categories grouped into 10 families: Ads, Dangerous, Free Time, Malware & Threats, Media, and Others. The tool’s default configuration blocks the most damaging categories, but operators can customize it to control the type of content accessed by users.
be.Safe essentials allows any IT reseller or CSP to provide internet protection to public service networks without additional investment, support centers, or training programs.
Why Teldat?
With be.Safe essentials, Teldat offers a cost-effective (cost effective) solution. As a basic unit, it is inexpensive to purchase, and does not specialist or highly-trained (highly skilled) staff to operate. Non-technical (non technical) staff can use the user-friendly interface to perform all necessary monitoring and control.
SMBs
SMBs have little budget for security and lack specific security expertise. They need inexpensive and easy-to-understand solutions
Challenge
As cybersecurity threats proliferate and become more sophisticated, they threaten small and medium businesses, and even residential users. This is increasingly true as their staff or students make increased use of the internet for SaaS or browsing.
Additionally, any organization that provides services to their staff or students must detect and manage inappropriate usage. This could be malevolent, and present a threat to security. Alternatively, it may be simply related to unauthorized, non-business-related websites which have a negative impact on productivity.
CSPs addressing these markets need the ability to add internet protection services without additional investment, support centers, or training programs.
Solution

be.Safe essentials provides a smart way to block 95% of the threat types currently encountered. SMBs can use it to apply rules to ensure that the internet is being used according to their needs and preferences. It provides easy-to-understand usage patterns and productivity analytics.
be.Safe essentials is a user-friendly solution that allows SMBs to control their cybersecurity risks and content policies for their employees. The tool is configured by default to block the most damaging categories, but everything can be customized.
Categories filter content control is based on 84 categories grouped into 10 families.
Why Teldat?
be.Safe essentials is the perfect tool /service for companies with low cybersecurity budgets seeking to avoid further future investment. It provides the first level of security; it is a must for cybersecurity, and it is affordable for all companies.
It can be consumed aaS, so requires no deployment, hardware, or cybersecurity knowledge.
Shopping centers
Most retailers regard Wi-Fi as a top priority for better customer service, but security is needed for both customers and staff.
Challenge
Shopping center businesses provide a branded retail experience and benefit from more sales opportunities through targeted advertising and data collection using Wi-Fi apps. They also want to set up secure administration networks for their own use, to connect EPOS machines, admin computers and IoT monitoring equipment like air quality sensors.
However, these operators must protect their networks from inappropriate or malicious activities performed by customers or staff, as well as third-party malware threats. The data captured by cybersecurity services can also help to improve staff productivity – this can be profiled by department, and periodic reports prepared about usage and protection statistics.
Solution

be.Safe essentials is a user-friendly solution that allows shopping center retailers to control their cybersecurity risks and content policies for their shoppers and staff. Content control is based on 84 categories grouped into 10 families: Ads, Dangerous, Free Time, Malware & Threats, Media, and Others. The tool’s default configuration blocks the most damaging categories, but operators can customize it to control the type of content accessed by users.
Operators can use be.Safe essentials aaS, accessing its omnichannel interface trough a website or mobile app. Staff can configure cybersecurity policies in seconds without deep cybersecurity knowledge.
Why Teldat?
be.Safe essentials is a cost-effective, CPE agnostic solution which is compatible with a large amout of currently deployed CPEs in companies, such as retailers. It can improve performance as it can be configured towards websites that benefit the shop’s productivity.
It can come as a Teldat-managed cloud SaaS solution to avoid installation and maintenance costs.
Read our latest Blog Posts
Security attacks on Supply Chains
In the digital age, supply chains are essential for the smooth functioning of businesses and the economy at large. Businesses increasingly rely on an interconnected ecosystem of suppliers, software and services to function. However, in recent years, we have witnessed...
Switches: Stacking/grouping/virtualization techniques
This blog post is the first in a series in which we will analyze the most notable technologies that we should take into account when selecting switches. Its aim is not to give a comprehensive description or follow any “didactic” order. One of the main characteristics...
The Cybersecurity Revolution: Artificial Intelligence and Machine Learning in Action
In the ever-changing and challenging cybersecurity scenario, one trend has emerged as a catalyst for change: the integration of Artificial Intelligence (AI) and Machine Learning (ML). These technologies are playing a pivotal role in fighting cyber threats, helping...