BLOG
Cybersecurity for Smart Grids: Protecting the energy infrastructure of the future
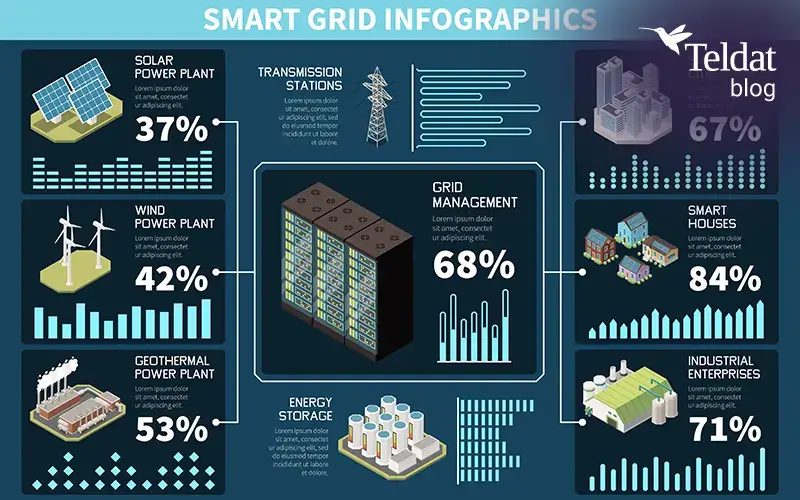
The digital transformation of the electricity sector has accelerated the adoption of Smart Grids: advanced energy infrastructures that integrate distributed generation, active demand response systems, and real-time bidirectional communication mechanisms enabled by digital technologies. This paradigm shift represents far more than a simple technological upgrade; it...
Kategorien
Heat Transfer in network equipment
Heat transfer is a crucial part of how any electronic equipment works. When devices are operating, their internal components generate heat, and that heat needs to be dissipated in a controlled way. Doing so ensures safe and reliable operation, helps maintain optimal...
From Firewalls to XDR: A Historical Journey Through Enterprise Cybersecurity
The Ever-Evolving Cyber Threat Landscape Over the past few decades, cybersecurity has undergone a profound transformation in response to an increasingly interconnected and digitalized world. What once revolved around basic perimeter defenses—such as traditional...
Quantum computing and the path towards secure Quantum SD-WAN
Quantum computing is no longer confined to research laboratories; it has emerged as a technological force with the potential to transform—and potentially undermine—digital security as we know it. Its rapid advancement is accelerating the arrival of a future in which...
Critical fleets are only as resilient as their connectivity
In critical fleet operations, vehicles aren’t standalone units anymore. Each one is a mobile part of a bigger digital system that relies on continuous, secure, real-time communications. Video streams, telemetry, location data, remote diagnostics, coordination with...
Reasons, beyond performance, to upgrade your network to Wi-Fi 7
When someone in IT proposes upgrading the wireless network, the standard reaction is: "But our Wi-Fi is already fast". Understandable most users measure network quality by a quick speed test. Yet, the move to Wi-Fi 7 is not just about chasing a bigger number on a...
Why the world is now looking to Europe to lead cybersecurity?
Over the past decade, cybersecurity has evolved from a specialized technical field into a core pillar of national resilience and executive responsibility. Today, boards and public administrations worldwide face a simple yet crucial question: Who can we trust to...
Increasing Cybersecurity Risks in IoT and Edge Computing in 2025
In 2025, the cybersecurity risks continues to undergo a drastic transformation due to the massive consolidation of IoT and Edge Computing. It’s not just about more connected devices — it’s about increasingly intelligent nodes with processing and decision-making...
A New Path to IPv6 Networks
The shortage of IPv4 addresses has accelerated the move toward IPv6. With roughly 4.3 billion possible addresses (32 bits), IPv4 can no longer meet the needs of modern connected devices. IPv6, by contrast, uses 128 bits—roughly 340 sextillion addresses—providing...
Private 5G networks for companies, public sector and operators
The adoption of a private 5G network has become a strategic pillar for companies, public institutions, and operators seeking secure, high-performance communication infrastructures under their full control. Unlike public networks, a private 5G network combines the...
SD-WAN Automation: The Secret to Large-Scale Deployments
Today’s corporate networks are undergoing rapid transformation. The digitization of processes, mass adoption of cloud applications, and the growth of remote work have made connectivity a strategic resource. SD-WAN has become a key technology, enabling traffic...
CE Marking – Certification and Marking
The certification of devices equipped with radio technology, together with their corresponding marking, has always been essential to ensure operational safety, electromagnetic compatibility, and the interoperability between systems. These processes were traditionally...
Post-Quantum Cryptography: The Future of Digital Security
Cryptography is the backbone of modern digital security, protecting everything from banking transactions to personal communications. However, advances in quantum computing threaten to break many of today’s cryptographic systems. This has spurred the development of...