be.OT Security
for OT environments
While when we speak about security, we tend to think in IT environments, it is not because these are the most vulnerable but because these are the most common. Industrial environments are also vulnerable.
Security in industrial environments

Today, Operational Technology (OT) systems suffer from the same traditional ills as Information Technology (IT) systems due to the convergence and connectivity both systems are experiencing.
-
- OT protection require specific and dedicated threat intelligence
- Security needs to be brought as close to the machinery as possible
- Stable nature of these networks allows for much more reliable forms of AI.
- Protocols, ports, … OT environments require specialized security products
- Adaptability is key. Old system coexists with new solutions.
Operational Technology Market Overview
From industrial to military necessity
Due to the increase in technology deployment in industrial platforms moving toward industry 4.0, the threat level of cyber-attacks raised due to the gravity of such at- tacks not only economically but possibly causing life casualties. This raise in technology deployment in the industrial field caused the cyber-criminals to focus their attacks on the used operation technologies OT as a new platform of attacks and gain.
Also due to the increase of automation and robotization of both the workplace and the production chain, these dependencies are only expected to grow. It is for this very reason, that both attacks and attackers have grown their complexity exponentially these past years. And this trend is only expected to grow. Even at a geopolitical level we are starting to see military interest in these types of attacks as a new weapon.
It’s for this reason that new security solutions are starting to appear in the market. By consolidating security solutions and providers the industry is looking to facilitate cross-environment integration. Organizations should strive to combine their OT and IT solutions and to consolidate around a smaller number of providers to reduce complexity and obtain a centralized view of all devices—both IT and OT. Organizations can reduce their risk and improve their security and operational efficiency by using integrated security solutions.
What are the important points related to OT

Dedicated threat intelligence
OT environments have different needs than the standard IT network. Since threats and attacks are going to be specific to the used protocols, ports, … so needs to be the intelligence to prevent them.

Near-edge security
In an OT environment there are thousands of IoT devices that communicate with each other and that are vulnerable to attack. Bringing security as close as possible to such devices is critical to prevent threat expansion.

AI on production… And on security
Recently, machine learning and AI models have found their way into the industrial environments as the fourth industrial revolution advances. In OT security, these techniques allow us to respond to zero-day attacks.
Integration and adaptability
OT environments are resistant to change, and for good reasons. Any security solution that might be implemented needs to be as adaptable and require as little changes as possible. Cloud is viable, but usually on-site approaches are preferred.
Understanding Operational Technology security
When talking about OT security, not only we are talking about different threats, but a complete change in paradigm as to how critical systems are, how they are deployed, updated and operated, what are the worst-case scenarios in case of failure, … The needs and requirements for this type of technology need not only a specific set of signatures, but a complete rethinking of how to implement a security solution.
Asset discovery for instance is not a trivially-solved issue. OT systems are usually complex, have been build over a timespan of several decades, and use a wide variety of devices that no one person in the organization fully knows. To add insult to injury, OT resources may be spread over multiple geographic locations, complicating the issue.
Network segmentation is also becoming fader every day. IT and OT networks are more inter-connected than ever, and this brings a whole new set of problems into the picture. Any centralized security solution must be able to handle both IT and OT threats to properly cover all scenarios that might affect this new architecture.
be.OT has been build from the ground up with these difficulties into consideration. Exploiting Teldat´s advanced networking capabilities and with our new security solutions in place, we are able to provide full visibility to our users though our state of the art NTA while providing a centralized, unified security solution that handles both OT and IT threats within a single system, providing our users a simplified, centralized screen in which all security and visibility issues can be addressed.

Solution & Teldat OT Products
The background
As we have seen, Operational Technology security does not just require a different set of signatures for different set of protocols, but a whole new approach to security. We are facing problems of asset discovery, dealing with old or really difficult to update systems, geographically distributed, …
Any solution that wants to operate within these parameters needs to be diverse enough and adaptable enough to properly respond to these challenges, as well as integrate with the very particular systems that any client might have.

Centralized management
& distributed security

The closer the security can be sent to each individual node of the network, the better. Sadly, with industrial systems, installing any security patch in the end devices is either impossible or prohibitive expensive. This is why be.OT engine offers a combined security system, bringing IDS / IPS capabilities to the networking equipment, as well as centralized security features if wished so.
This allows our clients to secure both the centralized traffic as well as bring as much control and segmentation closely to the different devices, while maintaining a single point of control through our central command console.
Level 7 visibility
Knowing what goes on inside a network with hundreds or even thousands of devices is not an easy task in any network. Outdated devices, constantly changing infrastructure due to devices malfunction or substitution, …. Monitoring these devices, controlling their conection and dataflows can be pivotal not only in the security but also on the management of an organization.
That is why within the solution ecosystem offered in be.OT we are including be.Safe XDR, our state-of-the-art NTA. Providing an out-of-the-box integration with our security engine, be.Safe XDR grants our users full visibility and traceability of their network. With a simple click, users can display monitoring dashboards, reinforced by a strong analytical engine that grants our clients the capacity to cross-reference any network dimension that flows through their network and beyond.

Zero-day attack prevention

Signature-based security is always the foundation upon which any security system is build. But, as powerful as it is, it has its vulnerabilities. Zero-day attacks are impossible to catch by these systems, and even a poorly-updated signature based system can mean a breach which attackers might exploit.
That is why be.OT offers added AI models for detecting abnormal activity within an OT network. While these models have had dubious results in IT networks due to their heterogeneity, this is not a problem that industrial systems have, since they are usually much more stable and reliable.
It is precisely this predictability that allows our AI models to work with such high levels of accuracy and low recall. Combined with be.Safe XDR, be.OT has thus the capacity to very accurately detect suspicious activity and raise an alarm for the security teams to be able to react quickly and preemptively in the face of any unforeseen threat.
OT Case Studies
Detection of suspicious activity and traffic on an OT network
Using threat detection platforms with AI techniques and monitoring to block OT attacks.
Control of access Internet for OT devices and users
Monitoring of traffic generated by OT devices to external networks and control of internal access from external equipment.
Detection of suspicious activity and traffic on an OT networks
Using threat detection platforms with AI techniques and monitoring to block OT attacks.
Challenge
Attackers can cause security breaches by infecting devices to spread malware over the network or act as bots to massively attack the organization itself or other companies. They can also steal credentials or gain unauthorized access to enter the network and try to get as much information as possible from the inside. This is what’s known as a lateral movement attack.
Solution

Traffic visualization and log analysis platforms make it possible to monitor everything that is going on in the network without generating a greater load on equipment or causing delays in communications. By having information on how the network usually behaves, traffic patterns are generated that allow anomalous behavior to be detected, such as multiple IPs accessing the same destination for a denial-of-service attack or attempts to access networks that are not allowed for a specific device.
In this way, automatic responses can be generated, disabling those suspicious devices suspected of having been infected or revoking access or credentials if they are detected attempting to access sensitive information when they shouldn’t, thus preventing them from achieving their goal.
Why Teldat?
Teldat’s be.OT solution analyzes all network behavior, applies Machine Learning and Artificial Intelligence techniques to detect suspicious behavior and detects and blocks any attack using specific signatures for OT environments.
Control of access Internet for OT devices and users
Monitoring of traffic generated by OT devices to external networks and control of internal access from external equipment.
Challenge
With the large increase in the number of devices in OT networks, information management is becoming increasingly complex as private networks are not always available making it necessary to provide access to public clouds for storage or log management and processing. On the other hand, employees may need access from external networks, with controlled access permissions to ensure no one gains control of the entire network from outside. An external DDoS attack or access attempt using outdated credentials can pose a serious security threat.
Solution
All traffic leaving the network can be controlled by means of security platforms, not only checking ports or IP addresses, or even hosts, but also using specific OT protocol signatures that allow access only to traffic that must be sent to the outside.
Similarly, secure access can be provided to the internal network through VPN connections to remote users, controlling access privileges to allow, for example, only SSH access to devices for monitoring or only allow reception of certain specific protocols to avoid information leaks.
Why Teldat?
Teldat’s be.OT solution supports more than 1000 application controls and IPS signatures for ICS OT. The intelligence provided through the industrial security solutions comes from the Teldat lab development team, which has been providing intelligence for corporate security applications for more than 30 years with the best security effectiveness and recognition in the industry.
OT networks and device monitoring
OT asset and device management with customized reporting and alert generation.
Challenge
OT networks can be made up of thousands or tens of thousands of devices sending traffic to various sources and with multiple hierarchical levels that complicate the management of access, inventory and network usage by the devices. Availability requirements are also critical, unlike in IT environments where delays may be permissible, so any alerts must be reported and corrected in the shortest possible time.
Solution

OT network management platforms should allow auditing of network behavior, detecting inappropriate behavior and assigning suitable thresholds for alerts that can be sent via email. Identifying the most active devices is very useful to optimize the deployed infrastructure and avoid potential bottlenecks that could slow down processes.
Simple management requires graphical visibility of connected devices to enable optimization and validation of connections. All this must be accompanied by the generation of periodic reports that group and synthesize information for quick and easy analysis.
Why Teldat?
Teldat’s be.OT solution parameterizes alarms to avoid false positives, generates network usage reports, allows visibility of both application and source/destination traffic, and provides detailed analysis of traffic patterns and usage trends.
Read our latest Blog Posts
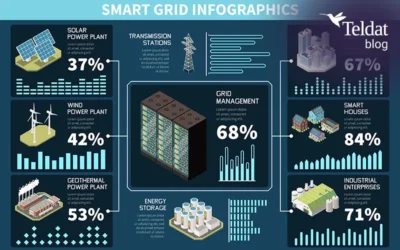
Cybersecurity for Smart Grids: Protecting the energy infrastructure of the future
The digital transformation of the electricity sector has accelerated the adoption of Smart Grids: advanced energy infrastructures that integrate distributed generation, active demand response systems, and real-time bidirectional communication mechanisms enabled by...
The benefits of smart metering for energy consumers and suppliers
Businesses of all sizes are under steady pressure to reduce their power consumption – not just to mitigate rising energy costs, but also to meet green legislation requirements. Besides, stakeholders like investors, employees and customers increasingly judge a company...
Telecommunications in industrial automation
Industry is currently undergoing a significant transformation due to the increasing adoption of automation. Ongoing technological advancements have led to the development of more efficient systems and processes, and the role of communications has been one of the key...