Secure Your Digital Transformation
Enhance communication security with SSE architecture, featuring Secure Web Gateway (SWG) and NGFW services that enable businesses, branch offices, retail locations, and remote workers to safely access full public internet connectivity.
Secure Traffic for Remote Sites

be.Safe Pro SSE enables remote workers to securely connect directly to the internet and cloud. It controls access by allowing or blocking connections and monitors data exchanges to detect and prevent harmful traffic.
- Ideal for businesses, branch offices remote staff, and retail locations.
- Enjoy all the benefits of cloud -based solutions
- Hardware agnostic, easy to configure, and requires no certifications.
- Scalable with a simple, “pay as you grow” deployment model.
- Manage security across entire networks of any size from a single console.
New possibilities, new threats

To stay competitive in today’s landscape, enterprises must continuously evolve their digital transformation efforts. Relying solely on an in-house data center is no longer enough, as employees can significantly enhance collaboration and productivity by accessing cloud-based SaaS tools like Office 365. In addition to corporate tools, employees often use a range of internet applications that simplify their daily tasks, making it essential to monitor these applications for security purposes.
Businesses in sectors like financial services, insurance, travel, distribution, healthcare, and administration—any industry relying on a network of geographically dispersed offices to serve local customers—generate significant additional traffic. These organizations need a modern approach that effectively addresses their evolving requirements. Fiber to the Home (FFTH) internet connections are growing in popularity due to their cost-effectiveness and the flexibility they provide. However, controlling these remote sites and enforcing consistent security policies across the organization is crucial.
The growing demand for greater scalability, flexibility, and more options is largely being addressed by migrating to SD-WAN networks. These networks offer clear advantages in terms of management, speed, agility, and WAN network flexibility, all while reducing costs. However, as the security parameter expands and security becomes a top priority, SDWAN technology alone does not inherently provide the necessary protection. This is where SASE seamlessly complements SD-WAN, paving the way for reliable, dynamic, and secure communications. SASE enables organizations to adopt security features at their own pace by integrating SD-WAN, Secure Web Gateways (SWG), and Next-Generation Firewalls (NGFW) in the cloud. This allows for scalability and real-time threat detection, stopping potential dangers before they reach the network.
As a result, organizations operating in this expanded, high-risk environment have an unprecedented need for robust security solutions.
Key Features of be.Safe Pro SSE Service
Direct Internet Connectivity
Secure web gateways enable companies with multiple branches to connect directly to the Internet and the cloud. This setup eliminates delays and bottlenecks at central points while ensuring traffic protection through secure tunnels. Additionally, by leveraging SD-WAN infrastructure, routing is optimized across multiple WAN links, delivering a comprehensive SASE solution.
Intrusion Prevention
Cloud security services prevent malware attacks, while NGFWs with intrusion prevention systems (IPSs, TP) defend against browser exploits and other threats. They utilize machine learning and AI analytics to assess visited sites and downloaded files for potential risks.

Cloud-Based Security Guard
SWGs act as intermediaries between users and web content, analyzing and securing traffic. They safeguard networks by allowing or blocking access to websites, applications, and file downloads based on security policies.

Firewall as a Service
Deploying NGFW as a service enhances traffic control beyond just applications and browsing. It adds a robust layer of security capable of blocking attacks within the network, safeguarding communication between remote sites, headquarters, and data centers.
Understanding Secure Cloud Services
Malware is constantly evolving, with new threats like phishing, spyware, crypto mining, and ransomware emerging daily. Routing all internet and cloud-bound traffic through an on-premise data center for security inspection can lead to congestion, latency, and downtime for users.
Cloud security services provide a solution by enabling companies with multiple remote locations and branches to connect directly to the internet and the cloud, either through non-corporate links or via SD-WAN infrastructure.
These services act as intermediaries between users and web content, analyzing and securing all traffic passing through them. Typically, they include features such as URL filtering, anti-malware detection and blocking, and application control. Like virtual security guards, they manage access to websites, applications, and file downloads, enforcing security policies from a centralized point. They offer medium-level security with centralized control over network protection.

be.Safe Pro SSE Teldat Solutions & Products
Teldat SASE Security as a Service
Remote users can achieve secure direct internet connectivity through either a traditional setup with local security elements in each office or a more advanced cloud-based solution. The cloud option stands out, offering continuous updates, instant deployment, unlimited scalability, and centralized management. Additionally, operating in service mode—Security as a Service—provides a low or even zero cost of ownership.
be.Safe Pro SSE is Teldat’s cloud security service. As part of a SASE platform, it integrates seamlessly with Teldat’s SD-WAN solution while remaining fully interoperable with non-SD-WAN technologies, thanks to its vendor-agnostic design. Unlike other security services, be.Safe Pro SSE features a unique private cloud infrastructure for each customer, ensuring no shared IP addresses and the ability to reserve cloud resources. This tailored setup ensures enhanced privacy, security and reliability, while also delivering the ease of deployment, scalability, and zero cost of ownership typical of cloud services.

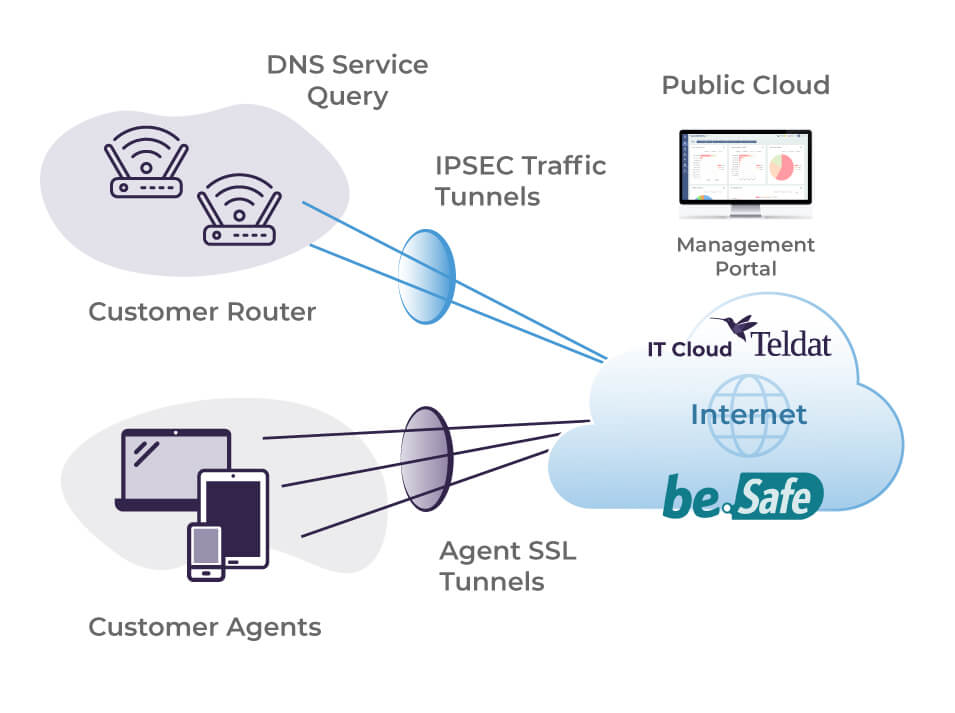
be.Safe Pro SSE Architecture
The be.Safe Pro SSE is a next-generation firewall optimized for cloud services, functioning as an internet gateway for branch offices and remote locations. Remote users connect securely through an IPSEC tunnel to send and receive internet traffic, while mobile users can access the service via an SSL VPN agent.
be.Safe Pro SSE not only controls access by allowing or denying connections based on the security reputation of sites and applications or established policies, but also analyzes the data being exchanged, preventing threats from reaching branch offices, remote locations, or other remote users.
This advanced level of security is ensured by its integration with the largest threat analysis databases on the internet, backed by the full capabilities of Teldat’s Threat Intelligence.
Key benefits
be.Safe Pro SSE is hardware agnostic and easy to configure. As a cloud-based solution, it offers scalability and seamless deployment, along with other cloud benefits such as fast processing times, continuous updates, and no maintenance or energy costs. Furthermore, it can be integrated with Teldat hardware that includes embedded security features.
Its scalable, ‘pay as you grow’ architecture creates a cohesive ecosystem with Teldat SD-WAN and Network Traffic Analysis (NTA), allowing customers to expand their infrastructure at their own pace. Maximum availability is guaranteed, as security features are dedicated to each client and not shared with others, thanks to the per-client logical separation implemented in the cloud environment.
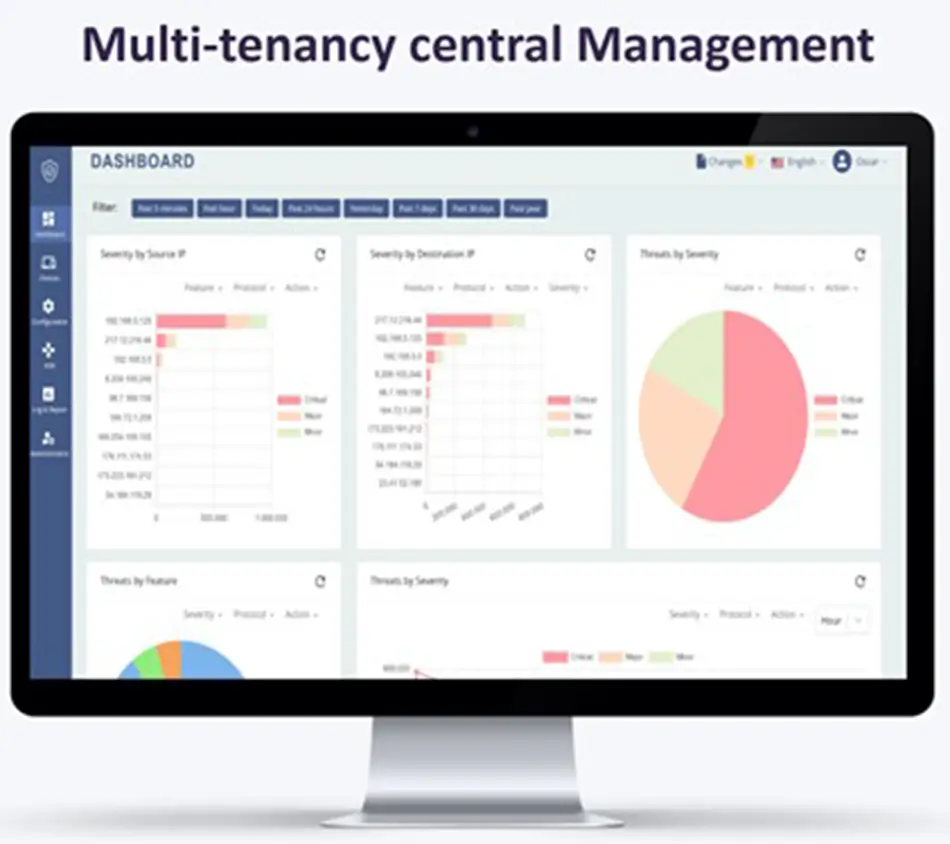
The entire network, regardless of size, can be managed effortlessly from a single security management console that requires only a web browser and internet connection. This console is integrated with the Teldat SD-WAN solution for unified network management but can also function in non-SD-WAN scenarios, supporting both Teldat and third-party routers through a simple IPsec tunnel configuration that accommodates dynamic addressing.
International certifications and truly global service

The be.Safe Pro SSE service leverages top-tier cloud providers to achieve minimal latency, with multiple points of presence across five continents.
Additionally, the solution not only meets but exceeds the stringent requirements established by internationally recognized standards and approval processes. It undergoes rigorous independent testing within the security industry, ensuring it adheres to the highest security benchmarks.
Use cases
Carrier providing security service
Carriers or system integrators with SMBs or small customers that require advanced attractively priced security but lack advanced knowledge of security.
Corporations securing their network
Big banks and other corporations requiring advanced security with all available NGFW features to manage external traffic with branches.
Carrier providing security service
Carriers or system integrators with SMBs or small customers that require advanced attractively priced security but lack advanced knowledge of security.
Challenge
Carriers and system integrators need to provide their users with an easy environment to configure their security. They seek to do this from a platform that they can share between customers to maximize return on their investment. They need a cloud-based solution that they can constantly update with the latest version and features, eliminating wasted time and money on managing updates, patches, and restarts.
Customers expect an ‘always connected’ service, with assured high availability at any time or location. They will also benefit from paying only for the services they use, depending on their budget and requirements. Offering a rollback option for when a service is not needed, so saving costs for users, is also an attractive benefit.
Solution

An effective solution for maximum security at the perimeters of these networks requires, in addition to web filtering capabilities, centralized solutions with IDS/IPS capabilities, antivirus, antispam, sandboxing, address reputation, DLP, SSL scanning, and email filtering, among others.
be.Safe Pro SSE is offered as an open management model; customer, CSP or shared. A cloud-based security solution means low demand for CPU resources in the DCE, and then an extended use of hardware.
be.Safe Pro SSE is deployed quickly aaS. The services offered by Teldat comprise a single contact point for both communications and security.
Why Teldat?
CSPs can seek new business opportunities by leveraging their installed base. be.Safe Pro SSE is hardware agnostic, and can be integrated with a Teldat SD-WAN or used as an isolated security service. It is also cost effective, making it attractive for SMBs and small customers with low security budgets.
Corporations securing their network
Big banks and other corporations requiring advanced security with all available NGFW features to manage external traffic with branches.
Challenge
Direct Cloud Access from branch offices and teleworkers is challenging, as centralized internet access is a drawback to users seeking access to public cloud services. However, when internet access is opened beyond the traditional centralized data center, the security perimeter is widened, and new security strategies are required.
This means that traffic from generic internet and other public sites must be filtered through a gateway which controls access to the corporation’s private network. Access to external applications must be controlled; controlled access must also be given to external parties and third-party companies.
Connections must be granted or denied depending on accessed sites’ security reputation, or on policies. Information exchanged can be analyzed to protect remote offices.
Solution
The cloud-based be.Safe Pro SSE solution supports access from anywhere, and allows a large bank or other corporation’s remote branches to connect to the internet securely. be.Safe Pro SSE users can connect safely to storage platforms, as the service controls the amount and type of information coming from the internal network to external applications.
Bank and corporate staff can connect with companies such as providers to share information or provide external services while accessing the corporate network securely and ensuring traffic interchanged.
Operation is simple as the integrated SD-WAN and security network can be run from a single pane of glass.
Why Teldat?
Using top-tier cloud providers, the service is offered at multiple points of presence spanning five continents, to ensure minimal latency.
A tied ecosystem with Teldat SD-WAN and NTA enables a tiered implementation at a controlled pace. The NGFW generates policies allowing communication between branches or among third parties.
Trains with security onboard
Train companies with security requirements for corporate network and passengers’ Wi-Fi onboard the rolling stock.
Challenge
Train operators set up SD-WANs over 4G or 5G and Wi-Fi for rolling stock connectivity. Passengers enjoy online services and internet browsing on their devices. Meanwhile, operatives can manage physical and network access control, and proactive onboard equipment maintenance.
However, security measures are essential to prevent train infrastructure attacks, from SD-WAN interception, connection of non-authorized devices or equipment to the network, unwanted traffic propagation, or malware downloads.
These events, plus unwanted web page access, hackers penetrating the network, or virus propagation into connected passenger devices all negatively impact the train operator’s reputation.
The passenger network and staff communication traffic must be secured onboard or in the data center.
Solution

be.Safe Pro SSE can be installed either in the data center receiving all the traffic, or in each rail carriage to provide security before traffic leaves the train.
The passenger network can be secured for any device, even in a densely-populated carriage with Wi-Fi 6 connectivity. Malware can be stopped before it can infect other passengers’ devices or give a bad image to the train company providing the digital service.
Similarly, communication over the staff network – even when it uses public connections – can be secured to protect corporate activities such as ticketing, maintenance, or operating CCTV security networks.
Why Teldat?
be.Safe Pro SSE NGFW solution can be deployed in the carriages, data center, or cloud. It can be deeply integrated with Teldat’s SD-WAN and hardware including the H2-Rail Router, which, with the new APR2044ax Wi-Fi 6 Access Point provide perfect connectivity onboard carriages.
Read our latest Blog Posts
Post-Quantum Cryptography: The Future of Digital Security
Cryptography is the backbone of modern digital security, protecting everything from banking transactions to personal communications. However, advances in quantum computing threaten to break many of today’s cryptographic systems. This has spurred the development of...
Threats to Cybersecurity in the Banking Sector
The digitalization of the financial sector has optimized service efficiency, remote access to banks and improved user experience. However, the risk of suffering cyberattacks has grown exponentially. In this context, cybersecurity has become a key strategic pillar for...
AI Under Attack: A Threat Evolving at the Speed of Technological Innovation
In 2025, Artificial Intelligence (AI) systems are not only tools for productivity, automation, and advanced analytics—they have also become new attack vectors for cybercriminals. From data manipulation to direct model exploitation, the threat landscape is evolving as...