Web browsing first began as a system lacking in privacy that allowed users to view simple content in text mode. Since then, the service has evolved in both functionality–allowing you to view complex designs–and in its access methods–said web content can be downloaded encrypted.
Web browsing first began as a system lacking in privacy that allowed users to view simple content in text mode. Since then, the service has evolved in both functionality–allowing you to view complex designs–and in its access methods–said web content can be downloaded encrypted.
According to Google, in January 2019, 96 of the top 100 Internet sites could be accessed through SSL/TLS (HTTPS). This protocol allows sending and receiving encrypted content, while improving privacy and security in the original HTTP protocol. Google also estimates that the penetration rate of SSL/TLS (HTTPS) protocol, used for accessing encrypted web content through its Chrome browser, is about 80% in 2019.
However, despite the good reception given to HTTPS, it does have some deficiencies that put Internet users’ privacy at risk. This is because, presently, the web domain that is browsed to still isn’t obfuscated.
This article discusses combining two techniques to obfuscate the web domains people visit, hence making it much more difficult for third parties to analyze traffic generated.
Part 1: DNS encryption
Internet browsing usually starts with what is known as domain name resolution. This resolution consists of translating a web name (www.example.com) into an IP address (55.55.55.55).
Domain resolution is done using a protocol called DNS (Domain Name Resolution). Unfortunately, DNS was originally defined without encryption, meaning that the domain names Internet users visit may be intercepted.
One of the next steps to safeguarding user privacy on the Internet is to upgrade to new versions of DNS servers that allow encrypted access through TLS or HTTPS. This will hide the domain name resolutions and close the first privacy gap.
The solution to this shortcoming is well underway – indeed, there are already as many approved definitions for these new techniques as implementations.
The new protocols are called DoH for DNS over HTTPS, defined in IETF’s RFC 8484 (https://tools.ietf.org/html/rfc8484), and DoT for DNS over TLS, defined in IETF’s RFC 7858 (https://tools.ietf.org/html/rfc7858).
It is also interesting to note that in September 2019, the popular Firefox browser announced that it plans to slowly enable DoH in its versions distributed in the US (https://blog.mozilla.org/futurereleases/2019/09/06/whats-next-in-making-dns-over-https-the-default/), directing them to servers operated by Cloudflare (https://support.mozilla.org/en-US/kb/firefox-dns-over-https).
Part 2: ESNI in TLS
Once you know the IP address of the website you want to visit, you can start browsing.
In the case of navigating using HTTPS, we have been persuaded through many means that this kind of navigation is secure. And yes, in a nutshell, it does provide secure, encrypted navigation. However, again, the name of the website being accessed is still sensitive to analysis.
This is because when a website is accessed through HTTPS, the certificate of the webpage being accessed must be checked. And said certificate is requested by indicating the domain that you want to access without encryption, through the SNI (Server Name Indication) extension located in the first SSL/TLS protocol packet. This is done because a web server may provide several different webs or services through the same IP.
The solution to this is currently being described (since 2018) in the IETF draft-ietf-tls-esni (https://tools.ietf.org/html/draft-ietf-tls-esni-04). This document specifies the method for ensuring the SNI field is sent encrypted in the first HTTPS packet, thus making it impossible to read. The new field used to send the encrypted SNI is called ESNI – Encrypted SNI.
The current proposal consists of distributing the keys and certificates to encrypt the SNI through the DNS protocol, but leaves open the possibility of using other channels.
Summary
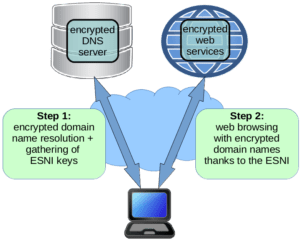
The combined use of the two techniques referred to above is summarized in the following figure.
As you can see, the encrypted DNS resolution is used to obtain the keys through which the ESNI is generated for subsequent web browsing.
The combination of these two techniques–DNS encryption and ESNI over TLS–means that the domain names used to navigate the web can always be kept private. One more step on the road towards a fully encrypted Internet.