Some countries switch off their telephone network in the near future. ALL IP is as previously mentioned one of the main buzz words. The shift to VoIP has already started and now is the right time to ask ourselves: “Do we need VoIP security?”
Some countries switch off their telephone network in the near future. ALL IP is as previously mentioned one of the main buzz words. The shift to VoIP has already started and now is the right time to ask ourselves: “Do we need VoIP security?”
VoIP security in this context doesn’t relate to firewalls, firewall problems in VoIP protocols or anything like that, but refers to the basic problem of wiretapping telephone calls.
Risks for a common network
As Internet telephony increases, the risk and security gaps caused by VoIP calls rise accordingly. While the classic telephony is carried out via a secure point to point connection and therefore, because of its structural point of view, offers a very high level of safety, VoIP uses for transmission the open IP network. In the ALL IP network data and voice communication melt together in one common network. Unlike the conventional fixed network, data will be divided into packages, transmitted separately and put together on the receiving end. However, VoIP calls are transmitted in one common data stream together with emails, web pages and other data to the receiver. All this offers on the one hand more flexibility but on the other hand risks potential weaknesses, if no additional security measures for voice data transmission are integrated.
Currently the need for security of contemporary communication doesn’t reflect the kind of VoIP transmission protocols in use. Even the most widespread SIP protocol (session initiation protocol) doesn’t include a secure authentication method or an encryption of the voice data. Protocols such as SIP are the basis for all Unified Communication solutions s and are therefore considered as the basis for offering IP voice services. VoIP connections via SIP without additional security measures/precautions while protocol information is being transferred unencrypted, can be completely seen by potential attackers.
Easy to spy
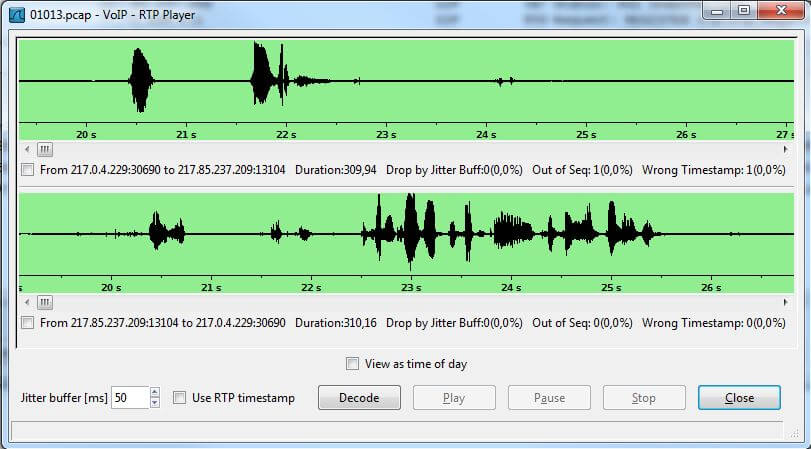
Tools for IP analysis are for free and easily available for anybody. A more or less standard is for instance WIRESHARK. This network protocol analyzer allows any computer user a gapless analysis of network data. At the touch of a button all telephone calls are displayed in real time. Name and phone number are displayed and each phone call can be intercepted.
There are no legal means to combat such espionage attacks, if companies don’t explicitly prohibit their employees the usage of such tools because the spy doesn’t have to overcome a criminal hurdle in order to put his plan into practice. In this case voice over IP is comparable to a car with unlocked doors, inserted ignition key and a running motor without surveillance in the street.
Does anyone need VoIP security?
In many interesting discussions with VoIP users it has become clear that most users don’t have any need for this kind of security. People are only alerted as soon as they get to know the circumstances and how easy it is to intercept a phone call. A typical example is home banking, just a quick transfer via Internet. Today nobody would do it via HTTP. HTTPS is a key prerequisite but not for phone calls. Dialing the home banking number, inserting the bank account number, carrying out the transfer – WIRESHARK even displays the dialed numbers in plain text.
Technical solutions
Taking the right safety-related and organizational measures into account, IP telephony is as secure as classical telephony for companies.
Security measures are carried out on different levels. IP telephony servers are protected by especially optimized operating systems, as well as firewalls and virus scanners. The encryption via SPS and SRTP is in particular mandatory in order to guarantee communication security. However, it is important to note that the simple telephone – the weakest link in the chain – supports these protocols. The phone call between a storekeeper and human resource manager is only secure if both telephones support these protocols. Initial suppliers announced to support SIPS and SRTP in the business-to-business segment in the future, but as long as this is not the case, VoVPN, for example, can be a solution for connecting home offices and locations.
Via VoVPN a VoIP connection can be set up though a VPN network. This makes sense in order to ensure the encryption of the VoIP traffic through an open network such as the Internet. VoVPN has been primarily developed because all protocols used until then didn’t support any encryption. Nevertheless, it is not a protocol as such, but describes methods of embedding VoIP streams into the VPN protocol.
Teldat is aware of this problem. The manufacturer supports its customers with its router portfolio, VoVPN solutions, SIPS as well as SRTP in the area of media gateways and pbx systems. Together with large telecommunication companies and suppliers, we have discussed these problems and implemented always the latest versions in order to guarantee our customers maximum security.