be.Safe Pro
NGFW Embedded Security
Teldat devices are specifically designed to seamlessly integrate with cloud services, providing advanced embedded security functionalities with NGFW (Next-Generation Firewall) technology. With the ability to scale from small remote offices to large corporate offices and even data centers, Teldat’s product range effortlessly caters to the diverse needs of businesses of all sizes.
Extending security to the remote device

Introducing beSafe Pro, a solution that brings advanced security features to Teldat’s latest range of devices. With beSafe Pro, companies will have access to enhanced capabilities to effectively block threats, segment and manage traffic flows within their premises, and monitor user and device activity.
- Ideal for remote locations, but also suitable for large offices.
- Single management panel that controls all devices.
- Simple and intuitive management, no need for expert personnel.
- Hassle-free deployment with zero-touch provisioning (ZTP).
- Enables quick alignment of security policies across all sites.
Meeting market demands: ensuring security for remote devices.
The needs of modern businesses have undergone a significant transformation. Gone are the days of homogeneous office spaces with user devices connected through private lines. Today, we are faced with a new reality of remote work, where residential internet connections and the proliferation of IoT devices have introduced heightened security challenges.
The demand for connectivity has surged, driven by the need for greater scalability and flexibility. As a result, businesses are increasingly adopting SD-WAN technologies, which offer clear advantages in terms of management, speed, agility, and greater freedom in the use of WAN networks, all while reducing costs. However, it is important to note that SD-WAN technology alone does not offer automatic protection against attacks or threats.
To address the security gap, additional security layers must be implemented. But this raises the question: How can we ensure a level of security that is comparable to a centralized security element?
There are two options here. Firstly, organizations can deploy distributed security devices locally at their branches. Secondly, businesses can subscribe to a cloud-based security solution that offers comprehensive security features.
The ideal solution will be one that effectively combines both aspects, enabling rapid adaptation to new threats. Furthermore, the solution should be effortlessly deployable and seamlessly integrated into a single remote communication device. It should be straightforward to implement, without impeding scalability. Moreover, it is essential that it can be managed centrally and in an integrated manner.
Important points to consider for remote device security.

Secure browsing
The advanced web filter technology consists of over 84 carefully curated browsing categories. Paired with a robust application control engine, it enables effective blocking of non-productive Internet categories and applications. Additionally, it provides comprehensive protection against accessing malicious websites or phishing pages.

Intrusion prevention
be.Safe Pro offers advanced protection against unauthorized access with its robust IPS/IDS engine. With a continually updated library of over 15,000 threat signatures, it ensures the security of users and IT systems by enabling real-time virtual patching of infrastructure. Moreover, be.Safe Pro provides comprehensive coverage with over a thousand attack signatures based on OT infrastructure protocols.
Centralized management
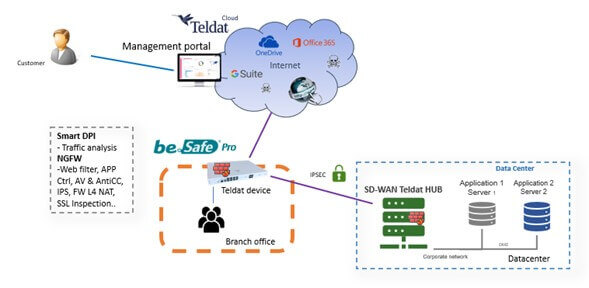
The management of all Teldat devices is easily and quickly carried out from a single cloud-based management console, regardless of the network’s size or the number of devices. For added flexibility, it can also be deployed virtually in a private cloud or data center.

Fast deployment and integration
All Teldat devices benefit from a straightforward deployment and provisioning process. With the help of ZTP technology, they can quickly assign a security profile and promptly apply the necessary policies and functionalities to protect the assets of remote locations within minutes.
Understanding security on remote devices
Today, the threat landscape is constantly expanding alongside increasingly sophisticated attacks, techniques, and malware. It is crucial to have robust protection against various cybersecurity threats such as phishing, spyware, cryptocurrency mining, and ransomware. However, the evolution in communications and the use of traditional MPLS lines, make it impractical to redirect internet and cloud traffic through a centralized customer data center for security inspection.
This leads to issues of latency and congestion, particularly for cloud-based applications like SaaS, ultimately impacting the user experience. Consequently, organizations have increasingly turned to internet access lines at remote locations, which presents an even greater threat to their security posture.
Distributed security, based on Next-Generation Firewalls (NGFW), serves as a safeguard, separating users from web content. By leveraging dedicated lines, it efficiently directs internet traffic while analyzing and ensuring the safety of data passing through the device. This comprehensive approach encompasses web filtering, malware detection, and application control. It seamlessly extends corporate security policies to remote devices, granting or denying access to websites and file downloads.
Teldat’s built-in security technology allows us to block fraudulent pages (phishing) in real-time, prevent malware attacks, and apply intrusion prevention systems (IPSs) to protect against browser or system attacks. Additionally, they utilize machine learning engines and threat intelligence to continuously update malware databases and categorize visited pages in real time.
NGFWs (Next-Generation Firewalls) provide advanced protection against a wide range of malware threats, including viruses, worms, trojans, spyware, adware, and ransomware. Their primary focus is to prevent malware attacks at the application level. One of the key advantages of NGFWs is their ability to virtually patch vulnerable systems even before a security update is released. Through ad-hoc signatures, they can proactively safeguard businesses by blocking known vulnerabilities. To ensure robust security measures, NGFWs are undoubtedly the optimal choice for businesses seeking high-level protection.
Teldat’s Remote Security Devices: Cutting-edge Solutions and Products
Teldat’s Remote Security Devices: Cutting-edge Solutions and Products
Teldat offers a comprehensive solution for security and communications. By leveraging the power of SD-WAN technology, Teldat ensures effective communication control. Furthermore, Teldat devices boast seamless integration of advanced security capabilities, some of which are embedded within the hardware.

Enhanced Performance and Seamless Integration with SD-WAN

Teldat devices are designed to safeguard user-generated traffic at headquarters, providing secure Internet access against advanced threats. With simplified yet robust management capabilities, Teldat ensures an exceptional user experience.
Teldat’s SD-WAN solution is seamlessly integrated, offering comprehensive features to enhance network performance. It has the capability to classify traffic at the application layer and intelligently route it based on predefined policies. This technology creates a virtual layer over traditional networks, utilizing MPLS lines, corporate Internet access, and even residential connections to automatically establish optimal paths for reaching services and applications.
Teldat’s SD-WAN actively monitors the network status of each application, intelligently selecting the optimal path and SD-WAN hub, all without any manual intervention. Furthermore, Teldat’s cloud-based network management and security platform allows for simple and fast deployment.
Architecture
Devices equipped with be.Safe Pro have the benefit of zero-touch provisioning, enabling fast and effortless deployment. By accessing the cloud-based management platform, the security configuration, including the allocation of a profile with required functionalities and network settings, can be easily downloaded. As a result, the service can be up and running within minutes.
The devices are designed to categorize traffic based on its application, allowing them to make informed decisions regarding whether to send it to the Internet for security measures or route it through the underlay towards the data center. This level of flexibility empowers the solution to seamlessly integrate into advanced communication architectures.
Fast and centralized management
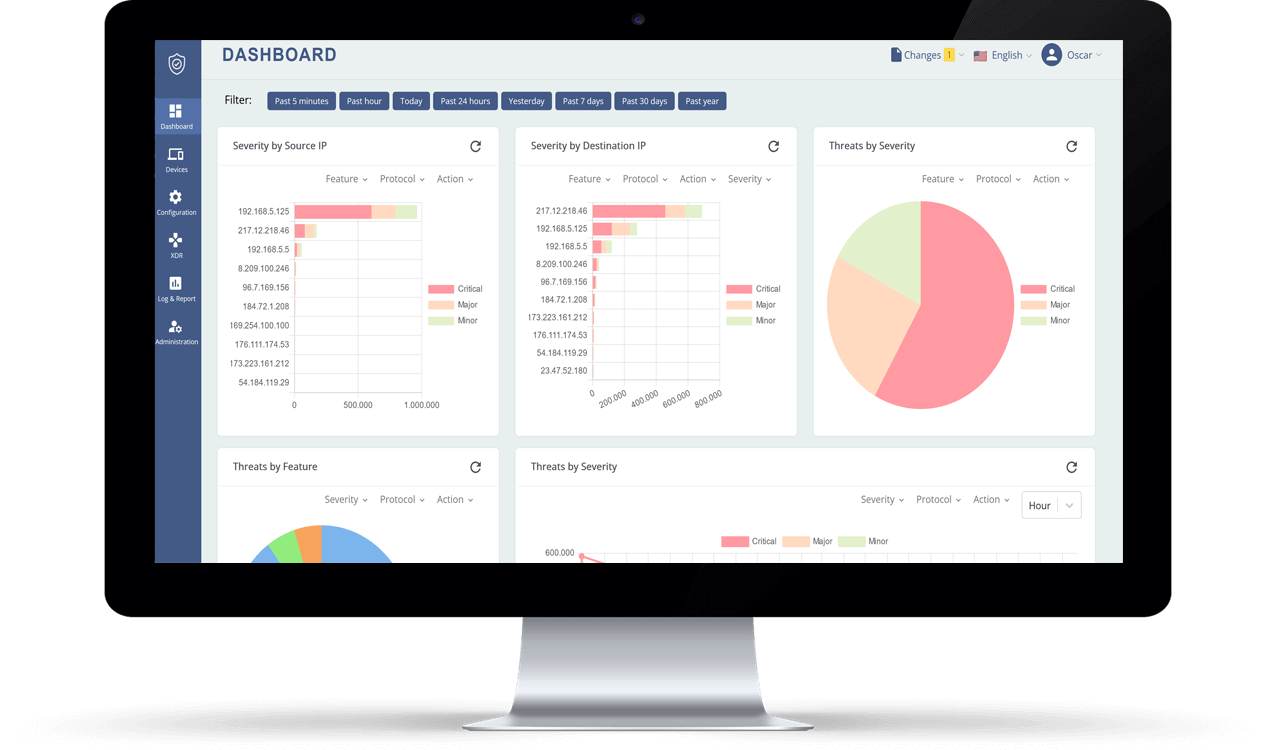
Teldat offers a seamless and rapid management solution for all its devices. Through a single console located in the cloud, regardless of the network scale or the number of devices, effortless control is achieved. Optionally, the system can also be deployed virtually in a private datacenter. Moreover, accessing the system is as simple as using a web browser with an Internet connection.
The interface provides us with easy access to all the necessary configurations, requiring minimal security knowledge. This not only saves time but also removes the need for specialized security personnel. Additionally, we have a comprehensive dashboard that displays detailed information about detected activity and threats, along with an event log and reporting feature.
Functionalities and equipment portfolio:
Cloud TI: All Teldat security products have access to the cloud service, which enables continuous updates and downloads of signatures and threat indicators. These devices provide robust protection against the latest global threats, leveraging multiple public and private sources.
SWG: The Secure Web Gateway offers advanced features such as categorizing internet browsing and applying web filtering to malicious categories. Additionally, it provides application control. With be.Safe Pro, users can benefit from a wide range of capabilities, including 84 navigation categories and more than 4,000 application decoders. This enables the creation of highly granular policies, even allowing for the generation of customized applications.
NGFW: The Next-Generation Firewall by Teldat allows us to implement traffic policies from level 4 to level 7. This means we can make informed decisions about allowing or blocking specific traffic flows, both to the Internet and between different locations. Moreover, by integrating our active directory agent, we can enhance our firewall rules by adding user identification.

IPS/IDS The Intrusion Prevention System/Intrusion Detection System is a powerful feature of Teldat. It employs a deep inspection engine that constantly updates its signatures to effectively identify and combat a wide range of threats, thus ensuring that the system remains vigilant against any new or evolving attacks. The devices also include a comprehensive Antivirus and Antibot engine, which operates at the flow level with specific signatures.
Remote Users/VPN: The system is equipped with a license that allows users to remotely access it via VPN. With the support of the IPsec protocol, you can use any open agent, including those already integrated into operating systems. Additionally, there is also the option to use a proprietary agent with SSL support.
SSL Inspection: Teldat devices possess the capability to uncover concealed threats within encrypted traffic by decrypting the data for thorough examination. To achieve this, they break the SSL tunnel, employing a trusted certificate authority (CA) to sign internet site certificates instantly.
Entry Level

RS420
Equipment aimed at small headquarters or companies, as well as IoT environments, where high bandwidths are not necessary (maximum 300Mbps), but good connectivity capabilities at low cost are required. 2 WAN ports and 4 LANs, with Wi-Fi 6 and 4G. SD-WAN compatible. RS420 device is capable of applying advanced security functionalities, such as IPS or Web filtering offered by be.Safe Pro.
Corporative

M2 Series
Geared towards corporate and medium-sized companies, with high needs in remote locations, including up to Giga capacity lines. The M2 has 2 WAN ports. One of them at 2.5Gbps. Fiber connection and Wi-Fi 6 interface. SD-WAN compatible. The M2 runs all the security functionalities of be.Safe Pro, allowing corporate policies to be applied in a centralized mode.

M10 Smarts Series
M10 raises level of connectivity. By incorporating 5G and Wi-Fi 6, organizations and medium-sized enterprises extend the range of operations without the need for cabling. It’s also possible to combine 5G with WAN lines and enables implementing SD-WAN configurations. M10 applies be.Safe Pro security functionalities to locally control threats and extend corporate policies to the remote site.
Hight Capacity

Atlas 840
High performance environments with SD-WAN. For central offices and medium-sized companies with high requirements. Incorporates 4 ports with 10Gbps. Acts as a hub and enforces security while keeping headquarter communications secure. Adopts advanced be.Safe Pro threat policies. Segments all headquarter environments, and with a high traffic encryption capacity.

Ares C640
Teldat flagship device. The Ares C640 takes communications for large sites or DataCenters one step further. It acts as an Edge, Hub or concentrator for all the company’s communications in environments of more than 10Gbps. Enforces advanced be.Safe Pro security policies. A first grade NGFW, segmenting the network and protecting data flows to and from the Internet.
Use Cases
Banking Sector
Banking institutions with thousands of branches and remote workers have to manage multiple types of Internet access providers.
Retail Market
Company with hundreds of small stores, in multiple locations: from shopping malls to isolated stores in small towns.
Banking Sector
Banking institutions with thousands of branches and remote workers have to manage multiple types of Internet access providers.
Challenge
Direct access to the cloud for remote and branch workers is a challenge, as centralized Internet access is an obstacle for users seeking access to public cloud services. However, when Internet access is opened up beyond the centralized data center, the security perimeter becomes larger and new security strategies are needed.
Connections must be allowed or denied based on the reputation of the sites accessed, information exchanged must be scanned to protect branch offices from attacks, viruses, malware and prevent leaks of confidential data.
It should also increase agility, optimize data management, provide network visibility at the application layer and reduce the cost of deploying new branches.
Solution

The be.Safe Pro solution allows access from anywhere and offers branches of large banks or companies the possibility of connecting to the Internet in a secure way. Users can connect to storage platforms, as the service controls the volume of data and the type of information coming from the internal network to external applications.
Staff can connect to third parties (such as suppliers) to share information or provide external services, while securely accessing the corporate network and ensuring that harmless traffic is exchanged.
The be.Safe Pro solution integrates with the SD-WAN network, so security and network management can be handled from a single control panel.
Why Teldat?
An ecosystem that combines Teldat’s SSE and SD-WAN allows you to create policies that enable communication between branches or third parties.
Securing all traffic: internal to each branch, intra-branch and outbound to the Internet.
Protection of remote users with ZTNA technology regardless of their type of access and location.
Retail Market
Company with hundreds of small stores, in multiple locations: from shopping malls to isolated stores in small towns.
Challenge
Provide maximum security for PoS device transactions, which manage bank data and must comply with current regulations and completely isolate the corporate network from the guest network, to prevent any kind of intrusion from the outside, or the spread of malware or spyware downloaded by a customer.
Misuse of public Wi-Fi networks by customers or employees can risk damaging the corporate brand. Ensuring that people are not accessing any illegal sites while browsing in-store is a key priority.
Agile deployments: communications are vital in the launch of a new store, equipment must work from the start without relying on specialized technicians for installation.
Solution

Centralized management in a single control panel for automatic deployment, rule configuration, troubleshooting and reporting.
Complete network segmentation to isolate each space and secure the perimeter. Complete analysis of network traffic to prevent malicious file downloads, improper use of browsing. Inter-store traffic is also protected, to prevent an infected device added to the network from spreading and causing business downtime.
Wide range of equipment for small stores with low bandwidth requirements, including Wi-Fi among its interfaces to offer all-terrain equipment, as well as for larger stores, always with a very competitive price-performance ratio.
Why Teldat?
More than 35 years of experience in all types of network deployments in the retail business sector, both for stores and supermarkets.
Cost-optimized devices with a wide range of performance to cover all security and bandwidth needs.
Network and security service provider
Carriers and system integrators with small or SME customers demanding security options at attractive prices.
Challenge
Carriers and system integrators must offer their users an easy environment in which to configure their security from a platform they can share with customers to maximize their return on investment. A cloud-based solution that they can constantly update, eliminating wasted time and saving money on upgrades, patches and reboots.
Customers expect an “always-on” service with guaranteed high availability. They also want to pay only for the services they use, based on their budget and requirements. Moreover, offering a “rollback” service when the service is not needed saves costs for the user
It is necessary to integrate security alerts into SOC tools such as SIEM that may already be installed.
Solution

be.Safe Pro offers a centralized solution and IDS/IPS, anti-virus, anti-spam, sandbox, IP address and URL reputation, DLP, SSL scanning, anti-spam, etc. All these capabilities available in a granular manner, allowing to choose the specific services demanded by the customer.
It also offers an open management model: client, service provider, or shared. It is rapidly deployed as a service (aaS) offering a single point of contact for communications and security. In addition, it can be integrated into existing infrastructure through query and provisioning APIs or syslog forwarding to SIEMs and other SOC tools.
Why Teldat?
Service providers can look for new business opportunities among their customers. be.Safe Pro is compatible with all types of hardware and can be integrated into a Teldat SD-WAN network or used as a standalone security service. It is also cost-effective, making it an attractive tool for customers with a limited security budget.
Lee nuestros últimos posts
Security attacks on Supply Chains
In the digital age, supply chains are essential for the smooth functioning of businesses and the economy at large. Businesses increasingly rely on an interconnected ecosystem of suppliers, software and services to function. However, in recent years, we have witnessed...
The importance of sequencing power domains in electronics
There is a clear trend in the electronics industry for integration, allowing for more compact and efficient designs. More and more, electronics manufacturers are making their chips smaller, including more components within their chips and extending the feature range....
Switches: Stacking/grouping/virtualization techniques
This blog post is the first in a series in which we will analyze the most notable technologies that we should take into account when selecting switches. Its aim is not to give a comprehensive description or follow any “didactic” order. One of the main characteristics...